
22 September 2022 – Cyberattacks can be prevented before an attacker is inside the internal network. Threat monitoring allows organisations to take action and properly neutralise a threat before it can exploit any existing vulnerabilities and affect the target institutions.
Kaspersky today unveils the results of its Digital Footprint Intelligence (DFI) report covering the external threats for a selection of countries from the Asia Pacific (APAC) region in 2021, including the six key countries Southeast Asia (SEA).
The report’s sole purpose is to create awareness about security threats, and demonstrate effective approaches to risk mitigation for widespread attacks with high business impact.
The rapidly growing share of adversaries’ initial access approach is the exploitation of 1-day vulnerabilities. Complicated business processes are forced to leave services on the perimeter, which in turn increases the external attack surface.
With the help of public sources and specialised search engines, Kaspersky collected information on 390,497 services available from public networks and analysed them for key security issues and vulnerabilities.
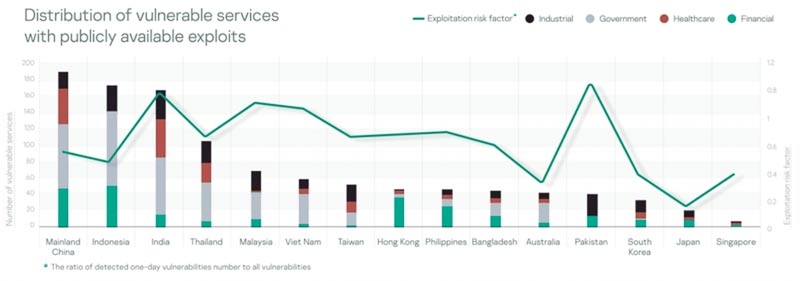
Analysis revealed that in 2021, almost every fifth of the vulnerable services contained more than one vulnerability, thereby increasing the chances of an attacker performing a successful attack.
All industry sectors, analysed in the report[1], in all countries have issues with application of security updates for publicly available services.
Government institutions (major personally identifiable information (PII) processors and providers of critical services for citizens) are potential incident-generators by a huge margin.
Singapore has a low number of vulnerabilities and an outstanding low ratio between the number of services and the sum of vulnerabilities in them, while Vietnam, Indonesia, Thailand and Malaysia have the highest ratio among SEA countries

In terms of the share of vulnerabilities with publicly available exploits, 3 countries out of TOP-5 are located in Southeast Asia (SEA) – these are Malaysia, Vietnam, and Philippines.
From Kaspersky’s practice in incident response handled by Global Emergency Response Team (GERT) and CISA advisory adversaries use a well-known list of vulnerabilities to exploit organisation defenses. While researching the security problems of companies from the APAC region, Kaspersky experts observed a number of commonly used vulnerabilities dubbed ProxyShell and ProxyLogon. Exploits for these vulnerabilities are easily available on the Internet, therefore, they can be easily exploited by even a low-skilled attacker.
While ProxyShell is quite common in China and in Vietnam, the countries most affected by ProxyLogon are:
ProxyShell is a group of vulnerabilities for Microsoft Exchange servers – CVE-2021-31206, CVE-2021-31207 , CVE-2021-34473, and CVE-2021-34523. ProxyLogon group includes CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, and CVE-2021-27065. The vulnerabilities from the both groups enable an actor to bypass authentication and execute code as a privileged user.
The best defense against these vulnerabilities is to keep public-faced systems updated with the latest patches and product versions. Companies should also avoid direct access to Exchange Server from the Internet.Kaspersky products protect against vulnerabilities from theboth groups – ProxyShell and Proxy-logon.
A great share of attackers’ initial accesses leading to cybersecurity incidents are related to services with remote access or management features. One of the best-known examples is RDP (Remote Desktop Protocol). It is Microsoft’s proprietary protocol that enables a user to connect to another computer through a network of computers running Windows.
RDP is widely used by both system administrators and less-technical users to control servers and other PCs remotely but this tool is also what intruders exploit to penetrate the target computer that usually houses important corporate resources.
Last year, Kaspersky monitored 16,003 remote access and management services available for exploit. Indonesia, India, Bangladesh, the Philippines, and Vietnam provide the maximum facilities for an attacker to gain remote access.
Government institutions are serving more than 40% of the attack surface for brute force attacks and credential leaks reuse.
“Clearly, cybercriminals are busy uncovering possible entry points in the region. From hunting for unpatched software, one-day vulnerabilities, and exploitable remote access and management services, malicious actors have a lot of options to infect lucrative industries. In short, a cyberattack is like a ticking bomb. While worrisome, reports such as our Digital Footprint Intelligence can be used as a tool to guide the cybersecurity capacity building of concerned organisations. If you know your weak areas, it’s easier to prioritise,” comments Chris Connell, Managing Director for Asia Pacific at Kaspersky.
To protect your businesses from such threats, Kaspersky experts also recommend that you:
Read the full Digital Footprint Intelligence report for APAC on Securelist.com.
[1] Financial, healthcare, industrial, governmental